It’s been more than 48 hours since Twitter was targeted in the largest hack of the company’s 14-year history. Yet, little is still known about how a hacker or group of hackers gained access to the accounts of former President Barack Obama, Elon Musk, and Kanye West, among others — some of the platform’s biggest verified users — in order to tweet out a Bitcoin scam.
But, one Twitter user involved in the infosec community has a very good idea about how at least one major part of the hack went down. So let’s break it down.
someone has managed to hack a slew of large verified twitter accounts to spread a bitcoin scam. they’ve made around $56k so far it seems… pic.twitter.com/wjjA7mHqCW
— Matt Binder (@MattBinder) July 15, 2020
Lucky225, a deceased hacker, and the Chelsea Manning connection
A security researcher who goes by the Twitter username Lucky225 penned a very interesting Medium post on Thursday detailing his own unique experience with the big Twitter hack.
Upon hearing about the attack on Wednesday, Lucky225 immediately checked on the status of one of the accounts he runs which has a rare Twitter handle, @6. These handles are often called an “OG username” due to the fact that they’re so short or generic that they had to have been registered during the early days of the platform.
Lucky225 administers the @6 Twitter account which once belonged to Adrian Lamo, who passed away in 2018.
If Lamo’s name sounds familiar to you, it’s because you’ve almost certainly heard of him before. Lamo was a big name in hacker circles in the early 2000s. But, in 2010, Lamo made news: He’d been informing U.S. authorities on Chelsea Manning’s role in providing Wikileaks with leaked classified information. This resulted in Manning’s arrest.
Upon looking into it, Lucky225 found that he had, indeed, been logged out of the @6 Twitter account, which Lamo’s family granted him permission to run.
It turns out, a few hours before verified Twitter accounts belonging to Microsoft founder Bill Gates and Amazon founder Jeff Bezos started tweeting about the same Bitcoin scam, Lucky225 received an email. The email wasn’t from Twitter; it was from Google Voice, informing him that a text message was sent concerning a password reset for Lamo’s @6 account. Lucky225 had not requested this reset.
Okay since I control @6‘s account, which got hit in this massive twitter account BTC scam I can give some insight, they’re either intercepting SMS on password reset or they’re bypassing it somehow. Got this Google Voice SMS code when the account was hacked which had OTP 2FA pic.twitter.com/yQflAUQL6x
— Lucky225🍀 2️⃣ 2️⃣ 5️⃣🍥 (@lucky225) July 15, 2020
What Twitter is telling us right now
As the hack was occurring on Wednesday, screenshots of what allegedly depicted Twitter’s internal admin panel, a sort of “master tool” the company uses to monitor and moderate user accounts, were being shared on the platform. It’s still unconfirmed if these were indeed authentic screencaps of the platform’s backend.
However, the belief is that with so many big users’ accounts being accessed at once, the hacker(s) almost assuredly didn’t use the usual methods of targeting each user via a phishing email or other classic social engineering methods. Whether the hackers had a contact on the inside of the company or an employee with admin access was socially engineered themselves is still unknown.
Here’s what we do know: In order to stop the attack and barrage of Bitcoin scam tweets coming from verified users’ accounts, the company locked down all verified accounts for a short period of time. (Even accounts that had attempted to change their password during the attack were locked out, with many still having issues getting back online.)
Twitter has since confirmed that around 130 verified users were affected by the attack. The company is also now saying that it doesn’t believe it’s necessary for users to change their account password as the hackers did not have access to account credentials. The investigation, however, is still ongoing. And Twitter isn’t saying much more than that quite yet.
How the hackers accessed those verified accounts
A new report published on Friday evening from the New York Times gives us a little more detail into how the admin panel could have been compromised.
According to the report, a hacker going by the name “Kirk” on the messaging service Discord had accessed the backend tool “when he found a way into Twitter’s internal Slack messaging channel” and found the credentials posted there. Kirk also discovered access to the company’s servers in the Slack board.
But, Lucky225’s experience with that Google Voice password reset may hold the key as to what exactly the hackers did once they were in Twitter’s admin panel. The fact that the attackers needed to reset the password for @6 before taking it over is pretty convincing evidence that tweets and password changes can’t be made from the admin panel.
So what is possible using that backend tool? According to Lucky225, there are two things that he believes can be done by those with Twitter’s admin access: changing the email address connected to the account and revoking two-factor authentication.
The hacker(s) were able to take over the @6 account through an emailed password reset without requiring the extra layer of security provided by the 2FA code that’s normally sent to the user’s phone.
Twitter effectively confirmed Lucky225’s suspicions later on. After he regained control of the @6 account, the company sent him an email stating that 2FA had been turned off for his account. He also received a request to change his password.
Then there’s also the curious matter of the SMS text message sent to his Google Voice number concerning the password reset on the day of the hack. As Lucky225 notes in his post: Did the hacker(s) not realize that turning off 2FA didn’t completely remove the phone record on file? Or is that something that just can’t be changed from the admin panel? It’s all unclear.
Why @6?
The last thing that I can directly answer for you right now is likely the question of why… why did the hacker(s) go after the old Twitter account of deceased hacker Adrian Lamo?
It’s quite simple really. As I mentioned earlier, @6 is an OG account.
In certain online circles, short generic social media usernames are a hot commodity. Often registered when a social media platform just launches, some view these handles as a status symbol. Much like with domain name speculation, these OG or “original gangster” accounts can sell for thousands of dollars in online forums and aftermarkets.
Just like with any other online economy, buying a social media handle could score you with a legit great, short name or it could leave you out of cash because you fell for a scam. For example, the forum OGusers is a notorious spot for sellers looking to pawn off OG accounts they’ve obtained through illegitimate means.
In fact, the previously mentioned Times report uncovered the information about how Kirk allegedly accessed the admin panel after speaking to a number of hackers who helped Kirk sell rare handles earlier in the day on OGusers.
On his website Krebs on Security, longtime cybersecurity reporter Brian Krebs points out how one now-suspended Twitter user going by the handle @shinji was tweeting about owning the @6 account while the hack was occurring on Wednesday.
A screenshot can be seen in the tweet above.
The New York Times report also confirms Brian Krebs’ investigation into who had gained control over the @6 Twitter handle. However, the Times discovered that this person, who provided his full name — Joseph O’Connor — had merely purchased the account on OGusers earlier that day under his username PlugWalkJoe. O’Connor is not the person responsible for hacking the account nor Twitter’s admin panel.
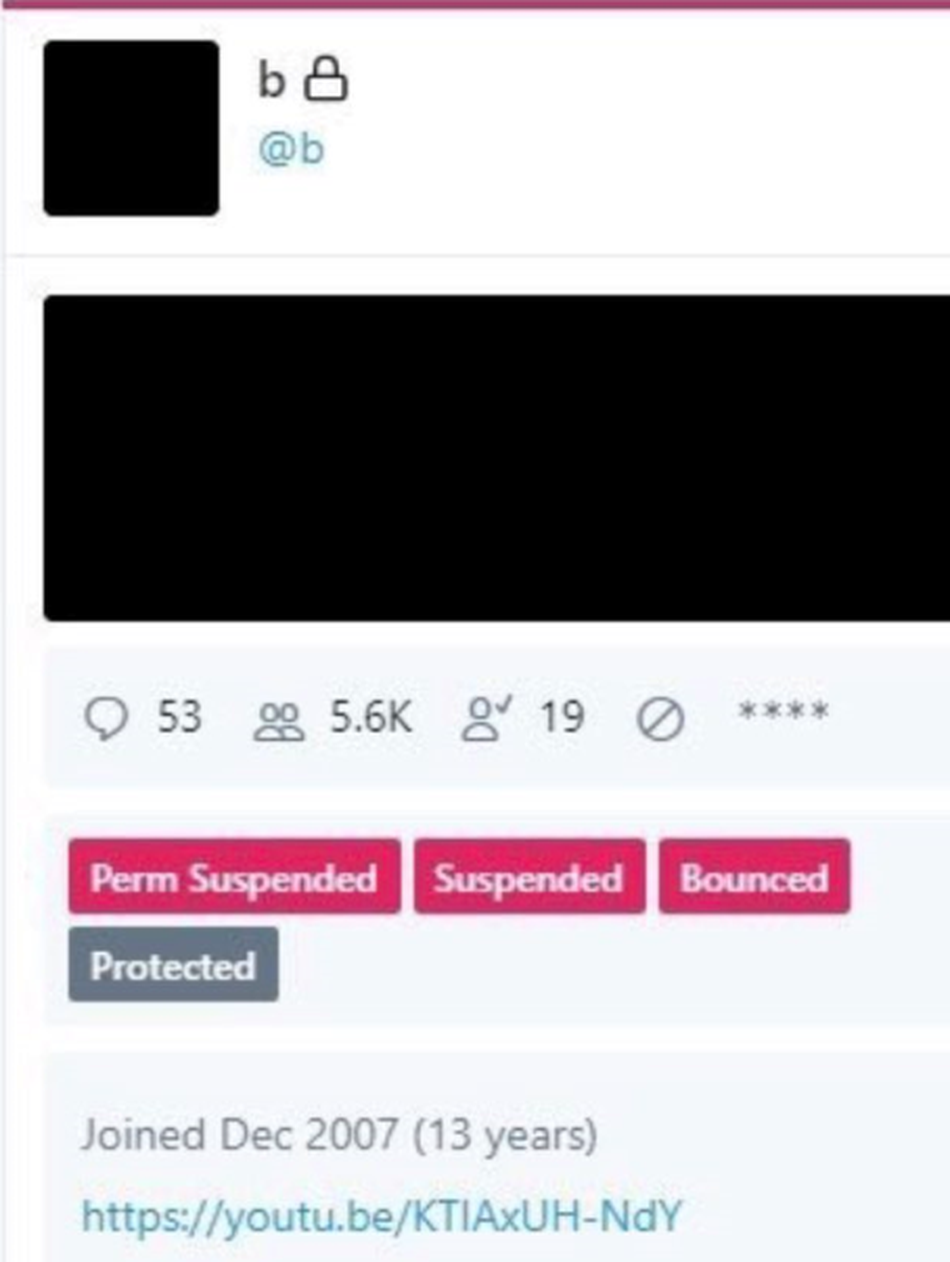
O’Connor had also previously boasted about owning OG accounts like @dead and @j0e. In addition to @shinji, other Twitter users were also posting screenshots purportedly from Twitter’s admin panel showing backend access to rare handles like the Twitter username @b.

A screenshot of user @B in the Twitter admin panel.
Image: twitter Screenshot: krebs on security
So, who was behind the attack?
Based on his experience, Lucky225 believes more than one hacker was involved in the Twitter breach. The @6 username had been stolen well before the Bitcoin scam started appearing on the timeline of verified accounts. Furthermore, the @6 account never sent a tweet about the Bitcoin scam in the first place.
Even with the latest report in the Times, it’s unclear if only Kirk was involved in the Twitter admin panel hack. After all, Kirk could be more than one person as well. However, we do know from the Times that there were multiple parties involved in the sale of the names stolen by Kirk.
As of now, exactly who is behind the attack on Twitter is all just speculation. The sales of these handles to multiple parties will certainly muddy the waters. Krebs, in his reporting from yesterday, said signs were pointing to O’Connor allegedly being involved in the attack somehow. Perhaps that can still turn out to be true. But the Times‘ latest investigation seems to refute that.
We simply don’t yet know who was behind the hack and it’s unclear if Twitter does, either.