Researchers have discovered a new type of destructive wiper malware affecting computers in Ukraine, making it at least the third strain of wiper to have hit Ukrainian systems since the Russian invasion began.
The malware, dubbed CaddyWiper, was found by researchers at Slovakia-based cybersecurity firm ESET, who shared details in a tweet thread posted Monday.
According to the researchers, the malware erases user data and partition information from any drives attached to a compromised machine. Sample code shared on Twitter suggests the malware corrupts files on the machine by overwriting them with null byte characters, making them unrecoverable.
“We know that if the wiper works, it will effectively render the system useless,” Jean-Ian Boutin, head of threat research at ESET, told The Verge. “However, it is unclear at this point what is the overall impact of this attack.”
So far, the number of cases in the wild appears to be small, and ESET’s research had observed one organization being targeted with CaddyWiper, Boutin said.
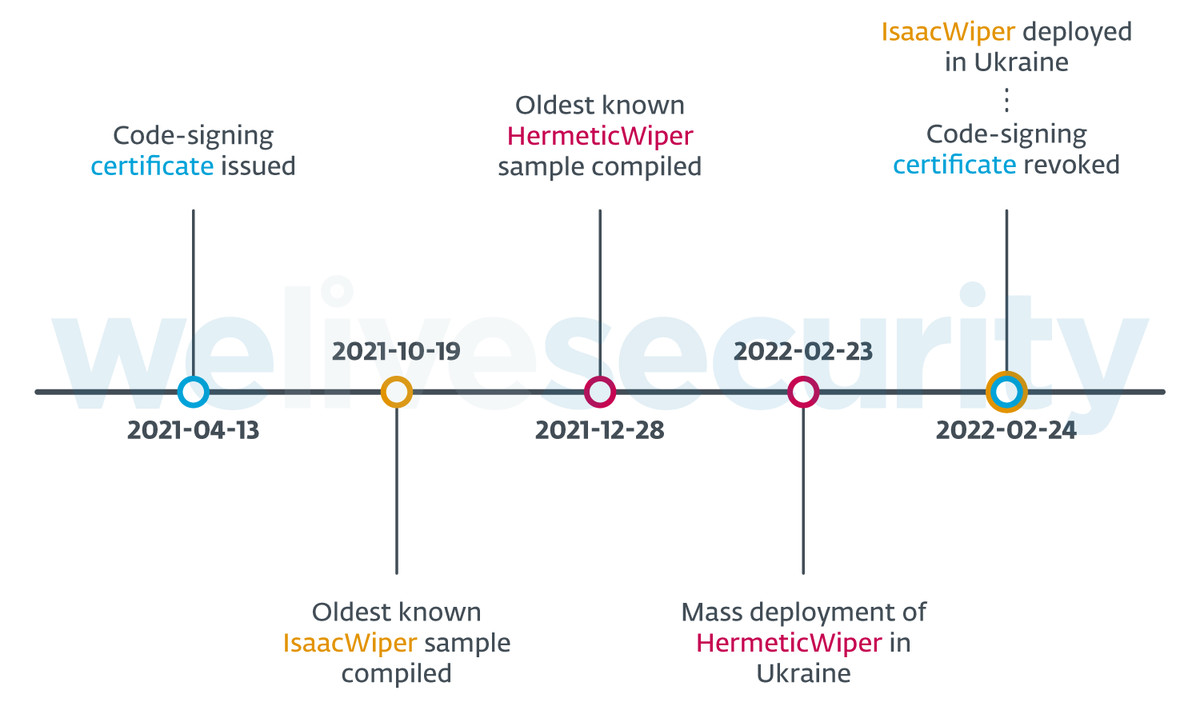
ESET research has previously uncovered two other strains of wiper malware targeting computers in Ukraine. The first strain, labeled HermeticWiper by researchers, was discovered on February 23rd, one day before Russia began the military invasion of Ukraine. Another wiper known as IsaacWiper was deployed in Ukraine on February 24th.
However, a timeline shared by ESET suggests that both IsaacWiper and HermeticWiper were in development for months before their release.
:no_upscale()/cdn.vox-cdn.com/uploads/chorus_asset/file/23315668/IsaacWiperTimeline.png)
Wiper programs share some similarities with ransomware in terms of their ability to access and modify files on a compromised system, but unlike ransomware — which encrypts data on a disk until a release fee is paid to attackers — wipers permanently delete disk data and give no way to recover it. This means the objective of the malware is purely to cause damage to the target rather than extract any financial reward for the attacker.
While pro-Russia hackers have used malware to destroy the data on Ukrainian computer systems, some hackers who support Ukraine have taken the opposite approach, leaking data from Russian businesses and government agencies as an offensive tactic.
Overall, large-scale cyberwarfare has so far failed to materialize in the Russia-Ukraine conflict, but it’s possible that larger attacks are still in store. In the US, the Cybersecurity and Infrastructure Agency (CISA) has published an advisory to organizations warning that they could be impacted by the same type of destructive malware being used in Ukraine.