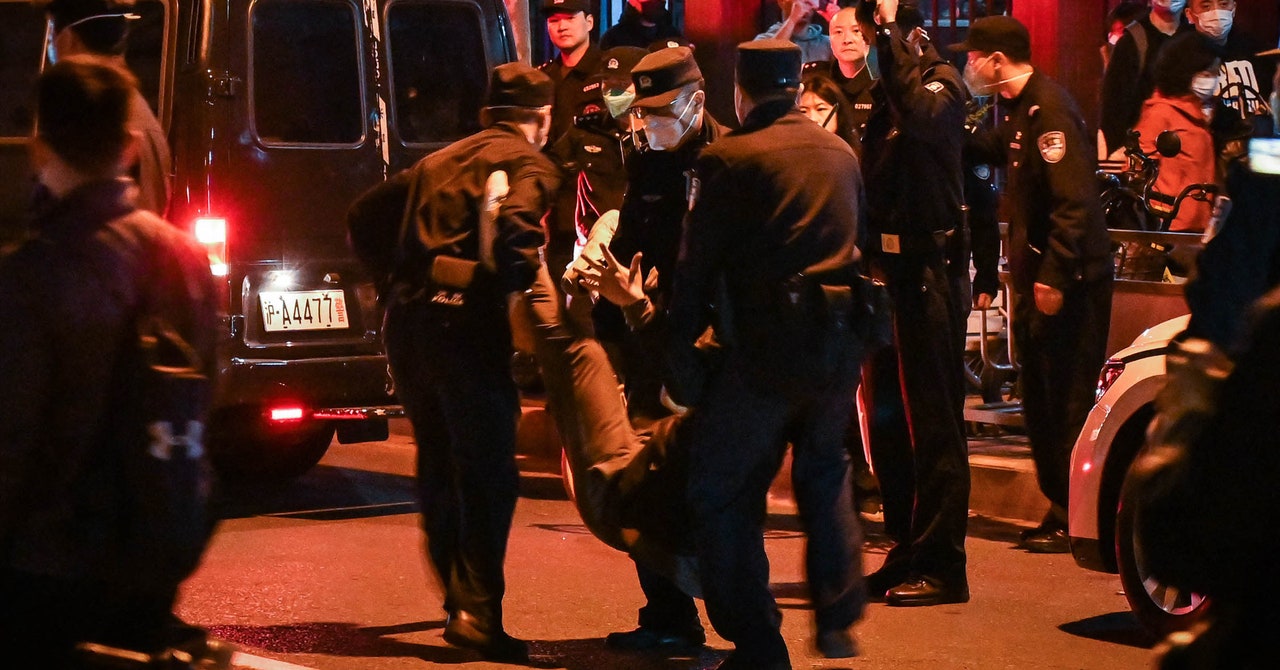
It was another busy week in security that saw big news about protests, surveillance, spyware, data breaches, and more. In the US, recent court filings detail how the FBI’s use of a controversial warrant yielded a trove of Google’s location data from thousands of devices in and around the Capitol on January 6. Meanwhile, in Iran, videos of antigovernment protests shared on social media highlight the importance of Twitter’s role in documenting human rights abuses and the consequences if the social media platform breaks.
On November 30, Google’s Threat Analysis Group moved to block a Spanish hacking framework that targets desktop computers. The exploitation framework, dubbed Heliconia, came to Google’s attention after a series of anonymous submissions to the Chrome bug reporting program. While Google, Microsoft, and Mozilla have all patched the Heliconia vulnerabilities, it’s a good reminder to keep your devices updated. Here’s what you need to know about all the important security updates released in the past month.
Google researchers also found this week that the encryption keys phone-makers use to verify software on their devices are genuine—including the Android operating system itself—were stolen and used in malware.
Finally, we published part six of WIRED reporter Andy Greenberg’s series, “The Hunt for the Dark Web’s Biggest Kingpin,” which chronicles the downfall of AlphaBay, the world’s largest dark-web marketplace. Read the final installment here, and check out the full book from which the series was excerpted, Tracers in the Dark: The Global Hunt for the Crime Lords of Cryptocurrency, available now from wherever you buy books.
And there’s more. Each week, we highlight the news we didn’t cover in-depth ourselves. Click on the headlines below to read the full stories.
A deadly fire in an apartment building sparked massive demonstrations in China where thousands of protestors in major cities have taken to the streets in defiance of the nation’s zero-Covid policy. The current wave of protests—the scale of which has not been seen in the country since the deadly 1989 Tiananmen Square protests—has been met with the massive surveillance and censorship apparatus that the state has been refining for decades. Authorities are using facial recognition, phone searches, and informants to identify, intimidate, and detain those who attended protests.
The protests are stress-testing China’s sophisticated censorship apparatus, and experts say that the sheer volume of video clips has likely overwhelmed China’s armies of censors. Leaked documents from China’s Cyberspace Administration called the protests a “Level I Internet Emergency Response,” and authorities ordered ecommerce platforms to limit the availability of VPNs and firewall-circumventing routers. On Sunday, Chinese-language Twitter accounts spammed the service with links to escort services alongside city names where protests were occurring to drown out information about the protests.
US Immigration and Customs Enforcement is in hot water after the agency mistakenly posted confidential data about thousands of asylum seekers during a routine update to their website. The data—which included the names, birthdates, nationalities, and detention locations of more than 6,000 individuals—was public for five hours before being taken down by the agency. The data disclosure could expose the immigrants affected by the breach to retaliation from the gangs and governments they had fled.
The agency’s tech negligence comes as the Biden administration is dramatically expanding the use of technology to monitor immigrants during conditional release through smartphone apps and ankle monitors.
“The US government has an obligation to hold asylum seekers’ names and information in confidence so they don’t face retaliation,” a lawyer at Human Rights First, the organization that discovered the leak, told the Los Angeles Times. “ICE’s publication of confidential data is illegal and ethically unconscionable, a mistake that must never be repeated.”
New research shows that Google continues to retain sensitive location data from individuals seeking abortions in spite of promises the company made in July to purge this kind of data from its systems. Researchers with Accountable Tech, an advocacy group, conducted various experiments to analyze the data that Google stores about individuals looking for abortions online. They found that searches for directions to abortion clinics on Google Maps, as well as the routes taken to visit Planned Parenthood locations, were stored by Google for weeks. Google spokesperson Winnie King told the Guardian that users “can turn Web & App Activity off at any time, delete all or part of their data manually, or choose to automatically delete the data on a rolling basis.”
Their findings contradict the pledges Google made after the US Supreme Court overturned Roe v Wade. “If our systems identify that someone has visited one of these places, we will delete these entries from Location History soon after they visit,” the company said in July. Five months later, Google appears to have not implemented this change.
LastPass, a popular password manager, is investigating a security incident after its systems were compromised for the second time this year. In a blog post about the incident, chief executive Karim Toubba said that an attacker gained access to their customers’ information using data stolen from LastPass’ systems in August, but did not specify what specific customer information was taken—although he stipulated that users’ stored passwords remained protected by the company’s encryption scheme. “We are working to understand the scope of the incident and identify what specific information has been accessed,” Toubba says. “In the meantime, we can confirm that LastPass products and services remain fully functional.”