Cellebrite was just put on notice.
The Israel-based company, which makes smartphone-hacking tools beloved by U.S. law enforcement and oppressive regimes around the world, failed to properly secure its own software — potentially compromising the integrity of all data gathered by its customers in the process.
That’s according to a brutal blog post from Signal founder Moxie Marlinspike, published Wednesday on the official Signal blog, which alleges serious security flaws in Cellebrite’s software.
“[We] were surprised to find that very little care seems to have been given to Cellebrite’s own software security,” he writes. “Industry-standard exploit mitigation defenses are missing, and many opportunities for exploitation are present.”
But wait, there’s more. Much more.
Moxies writes that it is possible for a specially configured file — for example, say, in the Signal app — to surreptitiously alter all past and future data collected by Cellebrite tools. Such a file would essentially render the Cellebrite software worse than worthless, as it could actively corrupt any data already pulled from confiscated smartphones.
In other words, if such a file were included in an app on a smartphone, and that phone was connected to Cellebrite software, then all bets are off.
“If they add the file to Signal, that would be interesting… as yes it would mean that they could probably nuke/hack/infect Cellebrite,” explained Patrick Wardle, the creator of Mac security website and tool suite Objective-See.
We reached out to Cellebrite, and asked if the company now considers phones loaded with Signal a risk.
“Cellebrite is committed to protecting the integrity of our customers’ data, and we continually audit and update our software in order to equip our customers with the best digital intelligence solutions available,” read the company’s reply in part.
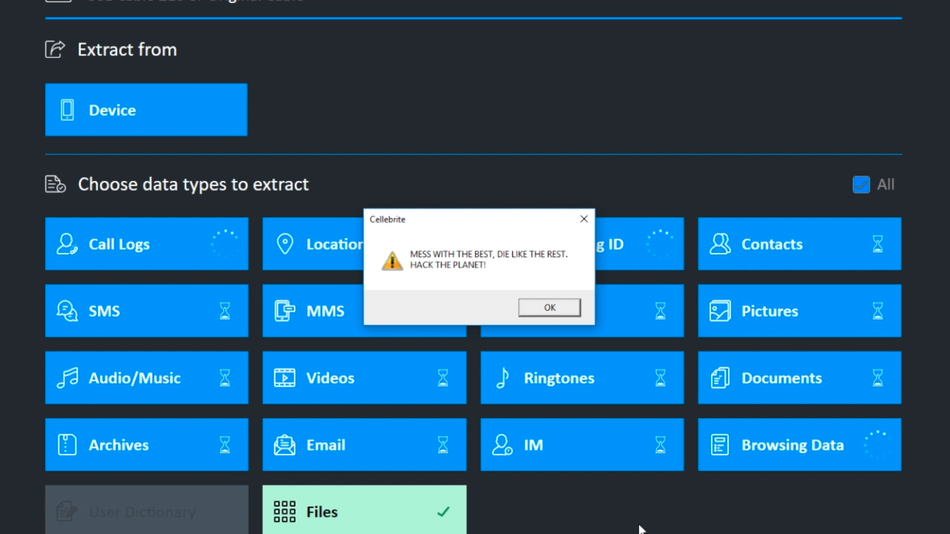
A video, included in the Signal blog post and incorporating scenes from the 1995 movie Hackers, shows one relatively harmless example of a potential exploit: a pop up on a Cellebrite device that reads, “MESS WITH THE BEST, DIE LIKE THE REST. HACK THE PLANET!”

Hack the planet.
Image: signal
Of course, if this were anything other than a demo, there likely wouldn’t be a notification. And the outcome might be more serious than a line from Hackers.
“Any app could contain such a file,” writes Moxie, “and until Cellebrite is able to accurately repair all vulnerabilities in its software with extremely high confidence, the only remedy a Cellebrite user has is to not scan devices.”
Dan Tentler, the executive founder of the security company Phobos Group, explained over email that Moxie’s findings mean that it’s now incredibly risky for government agents to use Cellebrite’s products.
“What agency would you like to exploit?” he asked rhetorically. “Bait one of them into reading a phone loaded with the exploit, and have the exploit then compromise the computer the Cellebrite platform is plugged into after the fact to retrieve the files.”
“What agency would you like to exploit?”
Notably, especially for Cellebrite and its customers, Moxie hints that future versions of Signal might incorporate the type of file he describes.
“In completely unrelated news, upcoming versions of Signal will be periodically fetching files to place in app storage,” he writes. “These files are never used for anything inside Signal and never interact with Signal software or data, but they look nice, and aesthetics are important in software.”
But will Signal actually do it?
“I think it’s more likely the [Signal] article [is meant to] bring awareness to the issue, and I would be surprised if the exploit / file is included,” wrote Wardle.
Tentler, for his part, sees Cellebrite’s alleged failure to get its security house in order as a part of a larger trend.
SEE ALSO: You can buy used Cellebrite iPhone hacking tools for cheap on eBay
“Cellebrite is just another vendor in the security space who makes a ‘security product’ but ‘does no security themselves,'” he wrote. “There will be many more of these to come — giving people a false sense of security pays big money, and a gigantic majority of the ‘information security industry’ falls into this category.”
Hack the planet, indeed.
UPDATE: April 21, 2021, 1:59 p.m. PDT: This story was updated to include comment from Patrick Wardle, the creator of Mac security website and tool suite Objective-See.
UPDATE: April 21, 2021, 3:39 p.m. PDT: This story was updated to include Cellebrite’s comment.