Popular daycare and childcare communications apps are “dangerously insecure,” according to newly published research, exposing children and parents to the risk of data breaches with lax security settings and permissive or outright misleading privacy policies.
The details come from a new report from the Electronic Frontier Foundation (EFF), which published the results of a months-long research project on Tuesday.
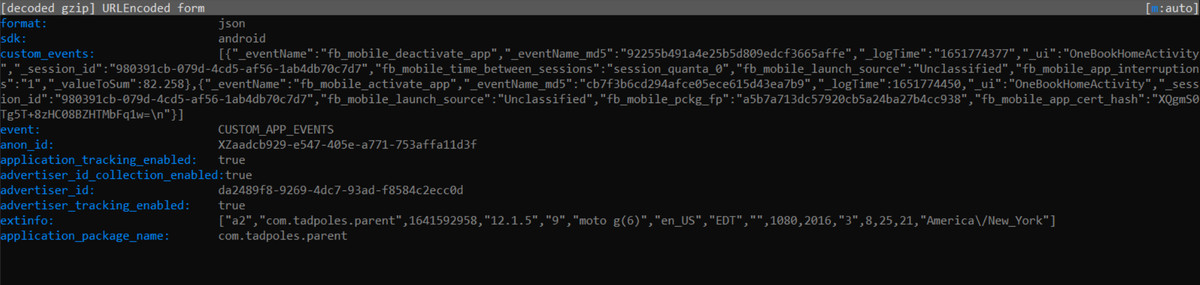
The research, conducted Alexis Hancock, EFF’s director of engineering for the Certbot project, found that popular apps like Brightwheel, HiMama, and Tadpoles lacked two-factor authentication (2FA), meaning that any malicious actor who was able to obtain a user’s password could log in remotely. Further analysis of application code revealed a number of other privacy-compromising features, including data sharing with Facebook and other third parties, that were not disclosed in privacy policies.
After being contacted by the EFF, Brightwheel implemented 2FA and claims to be ”the first in the early education industry to add this extra layer of security.” HiMama reportedly said that it would pass on the feature request to its design team but has not yet implemented the additional security feature. It is not known whether Tadpoles has an intention to implement 2FA.
:no_upscale()/cdn.vox-cdn.com/uploads/chorus_asset/file/23642462/tadpoles_fb_data.png)
Hancock started researching the privacy and security settings of various daycare apps after being asked to download Brightwheel when enrolling her two-year-old daughter in daycare for the first time. Hancock told The Verge that she initially enjoyed using the app to receive updates about her daughter but became concerned about a lack of security given the potentially sensitive nature of the information.
“At first there was a lot of comfort in seeing [my daughter] during the day, with the images they were sending me” Hancock said. “Then I was looking at the app like, huh, I don’t really see security controls I would normally see in most services like this.”
With a background in software development, Hancock was able to use a range of tools like Apktool and mitmproxy to analyze the application code and investigate network calls being made by each of the childcare apps, and she was surprised to find a number of easily fixable errors.
“I found trackers in a few apps. I found weak security policy, weak password policies,” Hancock said. “I found vulnerabilities that were very easy to fix as I went through some of the applications. Really just low hanging fruit.”
“I found vulnerabilities that were very easy to fix as I went through some of the applications. Really just low hanging fruit.”
The EFF’s new report is not the first to draw attention to serious flaws in applications trusted to keep children safe. For years, researchers have raised concerns over security weaknesses in baby monitor apps and associated hardware, with some of these weaknesses exploited by hackers to send messages to children. More broadly, a survey of 1,000 apps likely to be used by children found that more than two-thirds were sending personal information to the advertising industry.
Hancock hopes that reporting on these privacy and security flaws could lead to better regulation of child-focused apps — but nonetheless, the findings have left her concerned.
“It made me feel, as a parent, even more afraid for my child,” she said. “I don’t want her to have a data breach before she’s five. I’m doing all I can to make sure that doesn’t happen.”