Most services you use on your phone or laptop, from email providers to food delivery providers, require you to have a password. With so many services and websites, it’s hard to come up with unique passwords and remember all of them.
So, a lot of people end up using the same password for multiple services — and that’s a threat. If one website is compromised, your other accounts can be at risk too. A 2019 Verizon report suggests that 80% of hacking-related breaches are caused by using weak or compromised passwords.
That’s why the FIDO (Fast IDentity Online) Alliance is trying to get rid of passwords altogether.
The organization was founded in 2013 by Lenovo, Agnitio, Infineon, Nok Nok Labs, PayPal, and Validity Sensors. Since then a number of big-name partners such as Google, Apple, Microsoft, and Intel have joined the organization to support a password-less future.
I talked to Andrew Shikiar, executive director of the FIDO Alliance, and its partner and hardware security key maker Yubico, about authentication without passwords through the FIDO2 standard. But before we look at what companies are doing to allow users to login to services in different ways, let’s look at what FIDO2 is and how it works.
What is FIDO2?
To solve the problem of authentication through passwords, the World Wide Web Consortium (W3C) and FIDO Alliance came up with the FIDO2 standard. It’s a combination of W3C’s Web Authentication (WebAuthn) specification and FIDO Alliance’s corresponding Client-to-Authenticator Protocol (CTAP). This allows you to use your phone or laptop to identify yourself safely to a web service.
To reduce the risk of phishing or any other attacks, the FIDO2 method doesn’t involve storing your credentials on a server. Instead, it uses features such as biometric authentication to validate your identity so the password never leaves your device.
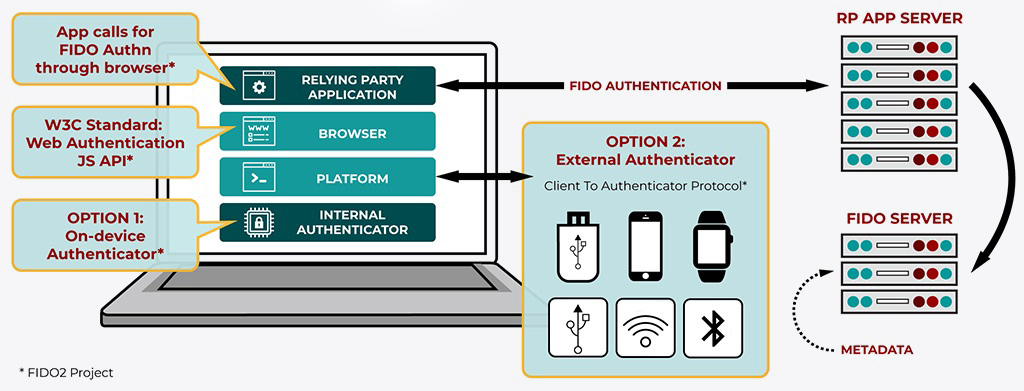
As shown in the diagram below, the WebAuthn part handles talking to services through browser or web services in a secure way. And CTAP allows you to use your phone to talk to WebAuthn and complete your authentication.
FIDO2 is also compatible with FIDO UAF and FIDO U2F-based hardware security keys. So, you can use a hardware key to login to services through your laptop or your phone. I’ve been using Yubico’s 5c NFC key for over a month to login to some services such as Microsoft accounts and Twitter through my phone and laptop.
How the alliance is working with companies to spread FIDO2
Andrew Shikiar, executive director of the FIDO alliance, believes that everyday devices such as phones play an important role in creating a password-less future:
Industry has found that public-key cryptography that allows consumers to use everyday devices is the preferred mechanism for stronger user authentication.
He said that if the authentication method is too hard, you’ll opt-out or find a way around it, and that’s the challenge FIDO is trying to overcome. It helps its partners with best practices and user-friendly ways to implement authentication through FIDO2 and other compatible standards.
Earlier this year, during its World Wide Developer Conference (WWDC), Apple announced that it was going to support the FIDO2 standard on iOS and macOS through Safari 14.

What that means is that you can use biometric methods (such as FaceID and Touch ID) or hardware keys (such as the ones from Yubico) to login to websites without a password.
Apple’s not the only one to adopt this, Google Chrome, Mozilla Firefox, and Microsoft Edge already support WebAuthn, and to some extent FIDO2.
Last year, FIDO Alliance declared Android as FIDO2 certified, paving the way for many devices to be used for authentication and allow users to login to services through biometrics. Later, Google started allowing users to login through biometric authentication to some of its services on Chrome for Android.
In addition to this, Microsoft’s Windows 10 is also FIDO2 approved. So, you can use its Windows Hello to login to a machine through facial recognition or a fingerprint scanner.
Security and productivity benefits
A lot of us use two-factor authentication (2FA) to login to our accounts. However, we still rely on SMS-based authentication, and that’s prone to attacks. Instead of that, FIDO2-based authentication allows you to use your phone or a hardware key, saving users a lot of time and effort. Plus, it’s more reliable and secure than SMS.
Often when I am logging into services like Twitter, I don’t get an authentication SMS for a long time. In these cases, if I use a hardware key as my secondary authentication, the whole process is very fast.

Shikiar said that FIDO2-based authentication is seeing a lot of traction with enterprise customers as well. Because of the COVID-19 pandemic, a lot of people have to work from home in an environment that might not be as secure as the office. Plus, with the rising number of cyberattacks this year, it’s important for companies to protect their data.
John Gilbert, General Manager, UK&I at Yubico, a company that makes FIDO-certified hardware security key, agrees:
Because of the pandemic, convergence between our work lives and our home is happening in a much more concentrated way. So there’s the need to ensure that we have the same sort of levels of security available to us. I think what Yubico does and what we’ve always done is to provide something that is very simple and easy to use.
The FIDO Alliance executive said that while it’s hard to know exactly what happened when Twitter was hacked in July, and accounts belonging to Elon Musk and Jeff Bezos were compromised, he believes that if the company had used security keys for sensitive programs, the breach wouldn’t have taken place.
Gilbert told me that hardware security keys are one of the most secure ways of authentication because they’re off the network and, unlike your phone, a hacker can’t attack them. Plus, these keys don’t rely on any kind of network or battery life. So, you can use them at any time.
A study from Yubico released last year suggested that an average employee spends almost 11 hours per year entering or resetting passwords, resulting in a productivity loss of millions of dollars. That figure can make a lot of enterprises think about going password-less.
Challenges to adopting a password-less future
Until now, FIDO’s standards have mostly been used as a second-factor authentication method in tandem with passwords. The alliance’s next challenge is to completely get rid of password or knowledge-based (login methods asking for details such as your pet’s name) mechanisms.
Some companies are now allowing customers to get rid of passwords. Last year, Japan’s networking giant NTT DOCOMO introduced password-less logins for its customers. CVS Health now has over 10 million customers who don’t use any password to attain its services.
Microsoft also allows customers to use biometric authentication or security keys on Windows 10 to login to some of its services such as Microsoft online accounts without passwords. I’ve used this service with Yubico’s key on a Windows machine and it works efficiently. eBay is also allowing customers to login using biometric authentication on iOS and Android.
While we’re starting to see some services adopting this kind of login, the majority of websites and apps still rely on passwords.
Another challenge is that not all desktop systems have biometric authentication. A lot of Windows 10-based laptops and Chromebooks allow you to login using a fingerprint scanner or a face recognition system that can be leveraged for authentication on websites too.
Apple has also started to include TouchID in recently released MacBooks. However, there’s a long way to go until the majority of desktop computers would feature some kind of biometric authentication.
It’s also important to convince users to move away from passwords, and it’s hard to change a habit that’s been instilled for years. That’s why FIDO is putting out educational material to instruct consumers and enterprises.
Gilbert believes that within the next year or so, we’ll see the industry consistently move towards embedding FIDO2 standards in operating systems and a range of applications it controls.
Shikiar is optimistic about the password-less future. He expects 90% of major web services to offer authentication that don’t require passwords within the next five years.
If this happens, it would be easier and far more secure for people to log in to services.
“What’s interesting is, I’m seeing that companies are quickly adopting password-less authentication, they’re looking at this not just as a security component, but also as a usability and brand building component. In the near future, it might put service to a competitive disadvantage if it doesn’t have a password-less login option,” he said.
Read next: Using jargon to sound smart? Science says you’re just insecure
