Microsoft president Brad Smith warned that the wide-ranging hack of the SolarWinds’ Orion IT software is “ongoing,” and that investigations reveal “an attack that is remarkable for its scope, sophistication and impact.” The breach targeted several US government agencies and is believed to have been carried out by Russian nation-state hackers.
Smith characterized the hack as “a moment of reckoning” and laid out in no uncertain terms just how large and how dangerous Microsoft believes the hack to be. It “represents an act of recklessness that created a serious technological vulnerability for the United States and the world,” Smith argues.
He believes that it “is not just an attack on specific targets, but on the trust and reliability of the world’s critical infrastructure in order to advance one nation’s intelligence agency.” Though the post stops short of explicitly accusing Russia, the implication is very clear. “The weeks ahead will provide mounting and we believe indisputable evidence about the source of these recent attacks,” according to Smith.
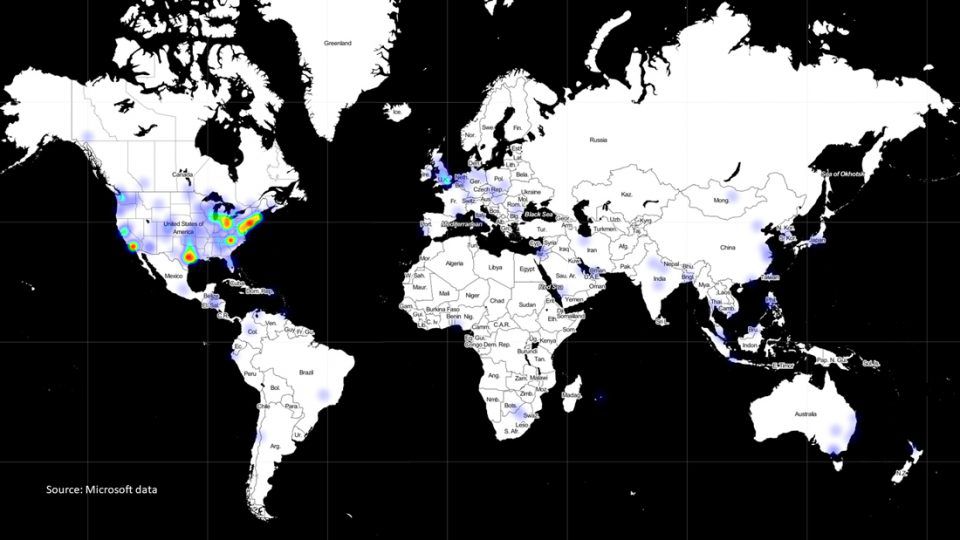
To illustrate just how far-reaching the hack was, Smith included a map that used telemetry taken from Microsoft’s Defender Anti-Virus software to show people who had installed versions of the Orion software that contained malware from the hackers.
:no_upscale()/cdn.vox-cdn.com/uploads/chorus_asset/file/22181335/cyber1_960x540.jpg)
Microsoft has also been working this week to notify “more than 40 customers that the attackers targeted more precisely and compromised through additional and sophisticated measures,” according to Smith. Approximately 80 percent of those customers are located in the US, but Microsoft also identified victims in Canada, Mexico, Belgium, Spain, the UK, Israel, and the UAE. “It’s certain that the number and location of victims will keep growing,” Smith said.
Investigations into the hack are ongoing. The Federal Bureau of Investigation (FBI), the Cybersecurity and Infrastructure Security Agency (CISA), and the Office of the Director of National Intelligence (ODNI) issued a joint statement on Wednesday to say that they were coordinating a “whole-of-government response to this significant cyber incident.” And Smith warned that “we should all be prepared for stories about additional victims in the public sector and other enterprises and organizations.”
Earlier on Thursday, Reuters reported that Microsoft had been hacked as part of the breach and that “it also had its own products leveraged to further the attacks on others.” But Microsoft denied that claim in a statement to The Verge:
Like other SolarWinds customers, we have been actively looking for indicators of this actor and can confirm that we detected malicious Solar Winds binaries in our environment, which we isolated and removed. We have not found evidence of access to production services or customer data. Our investigations, which are ongoing, have found absolutely no indications that our systems were used to attack others.
Microsoft has been responding to the hack since December 13th, including blocking versions of SolarWinds Orion that contained the malware. Microsoft and a coalition of tech companies also seized control a domain that played a key role in the SolarWinds breach, ZDNet reported.
SolarWinds has also taken the step of hiding a list of high-profile clients from its website, perhaps to protect them from negative publicity. The list included more than 425 of the companies on the Fortune 500.
As for Microsoft, Smith used his post to call for a more organized, communal response against cyberattacks, both at a government level and amongst private institutions. “We need a more effective national and global strategy to protect against cyberattacks,” he writes. Microsoft is also looking for “stronger steps to hold nation-states accountable for cyberattacks.”