
I gave Roku a bit of a hard time in March after it came to light that some 15,000 accounts were affected in a security breach. To be fair, that breach wasn’t entirely Roku’s fault because it was done via credential stuffing. That’s the method by which credentials are used from some other leak and just tried in various other services in hopes that you’ve reused a password somewhere. That attack netted more than 15,000 hits.
That’s bad enough. Worse was that Roku still didn’t have two-factor authentication, which would have required the evildoers to have a second set of credentials and could have prevented many of the unauthorized entries.
But apparently things actually got worse from there. Roku today announced that the investigation into the 15,000-account breach uncovered a second attack, “which impacted approximately 576,000 additional accounts.” (For context, Roku had 80 million active accounts at the end of 2023.)
Like the first attack, Roku says that “it is likely that login credentials used in these attacks were taken from another source, like another online account, where the affected users may have used the same credentials.” In other words, more credential stuffing. Roku says that fewer than 400 cases saw unauthorized purchases or streaming subscriptions using the payment methods that were attached to those accounts.
All of that is bad. Very bad, actually. (Especially for the 400 accounts that actually saw money change hands.)
Roku finally enables 2FA, sort of
If there’s any good news to come from this, is that’s Roku has finally enabled two-factor authentication. Sort of. First, here’s what Roku had to say in its post announcing the second breach:
“As a part of our ongoing commitment to information security, we have enabled two-factor authentication (2FA) for all Roku accounts, even for those that have not been impacted by these recent incidents. As a result, the next time you attempt to log in to your Roku account online, a verification link will be sent to the email address associated with your account, and you will need to click the link in the email before you can access the account.”
That second part is important. The main two-factor authentication Roku has implemented is that it will send you a link, via email, as the secondary form of authentication. That’s better than nothing. You also can enter the last five digits of your device ID if for some reason you can’t get to your email to click the link.
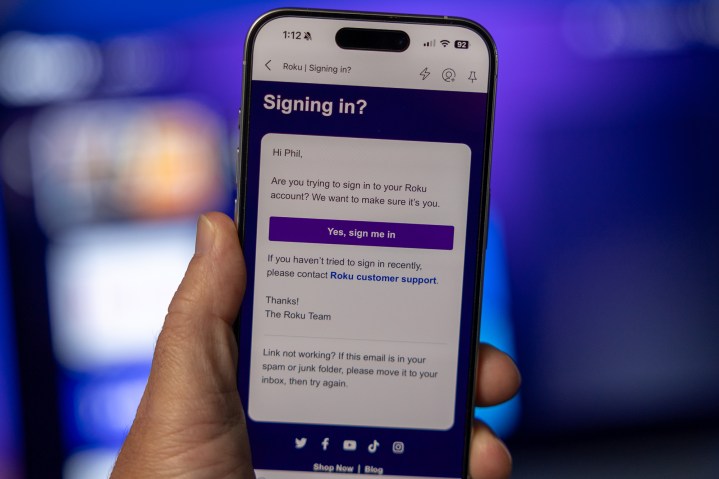
What you don’t get is any options. You can’t choose whether the two-factor authentication is done by “magic link” (wherein the company sends you a temporary link to approve access), or time-based code via SMS or authenticator app. Or some other method. That’s not the end of the world, I suppose. An emailed link is fairly frictionless — provided that the email account itself isn’t also compromised.
But it’s also not without issues.
Post-2FA device activation
Just to test things out, I reset my Roku account password. All subsequent logins have ended up with Roku sending me a email with a link to click, just like Roku said would happen. That works fine in a web browser. I log in with my email and password, then wait a couple seconds for Roku to send me a link to click. Same goes for logging in to the Roku app.
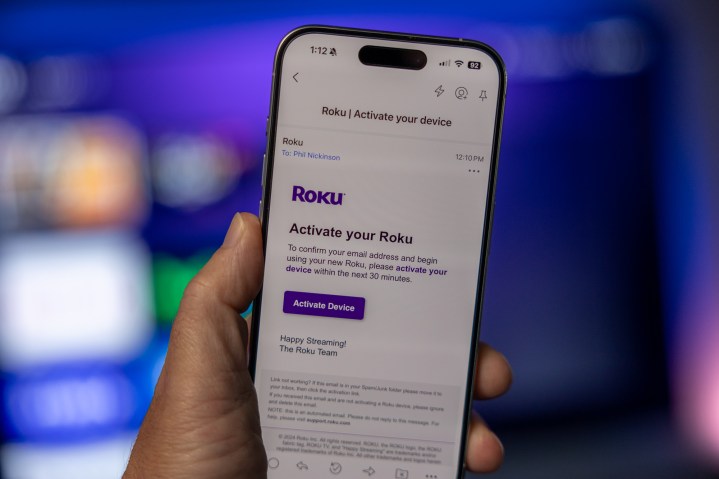
But I ran into issues trying to log in to a Roku streaming stick after a hard reset. There are two options here. With one, the Roku device can display a QR code on the TV. Scan it with your phone, and you’re prompted to log in using your email and password. Easy enough. And that login will send you a link via email that you have to click before you’re actually able to do anything on the device you’re trying to activate. Only, it doesn’t appear that the authentication is returned to the device.
But if you choose the option by which you manually type your email using the Roku remote, you’ll be sent a different-looking email. Click that link, and your Roku device will authenticate and activate, just as it should. In other words, it looks like the QR code method is trying to log you in to your account, while the manual method is trying to properly activate the device.
Roku says it’s looking into this part.
The really frustrating part
This really shouldn’t be that difficult. Two-factor authentication is not particularly new. And while any 2FA obviously adds a layer of complexity to any login scheme — and if Roku is known for anything, it’s simplicity — 2FA is also the sort of thing that users have gotten used to over the years.
Roku needs to do a few things. Foremost is that it needs to fix the device authentication. It’s simply broken if you try to use the QR code. (The good news is that should be a server-side fix.) It should allow you to choose your method of authentication. That likely would take a little longer to roll out. But given that Roku should have had proper 2FA set up years ago, that’s hardly an excuse.
Security is always going to be an uphill battle. It’s too easy for the bad guys to play offense. Defense is costly and time-consuming. But it’s not getting any less important. Roku still needs to do better.
Services Marketplace – Listings, Bookings & Reviews
