It seems Tesla isn’t taking full care of its customers’ personal data when replacing infotainment and Autopilot hardware in some of its vehicles.
According to an investigation by white hat hacker, GreenTheOnly, previously used Tesla infotainment components have been found for sale online. The real kicker though, is that Tesla isn’t wiping the past customer’s personal data from the hardware before passing them on, InsideEVs reports.
[Read: Tesla pulls a slick sales move in China, lowers Model 3 price to fit new subsidy limit]
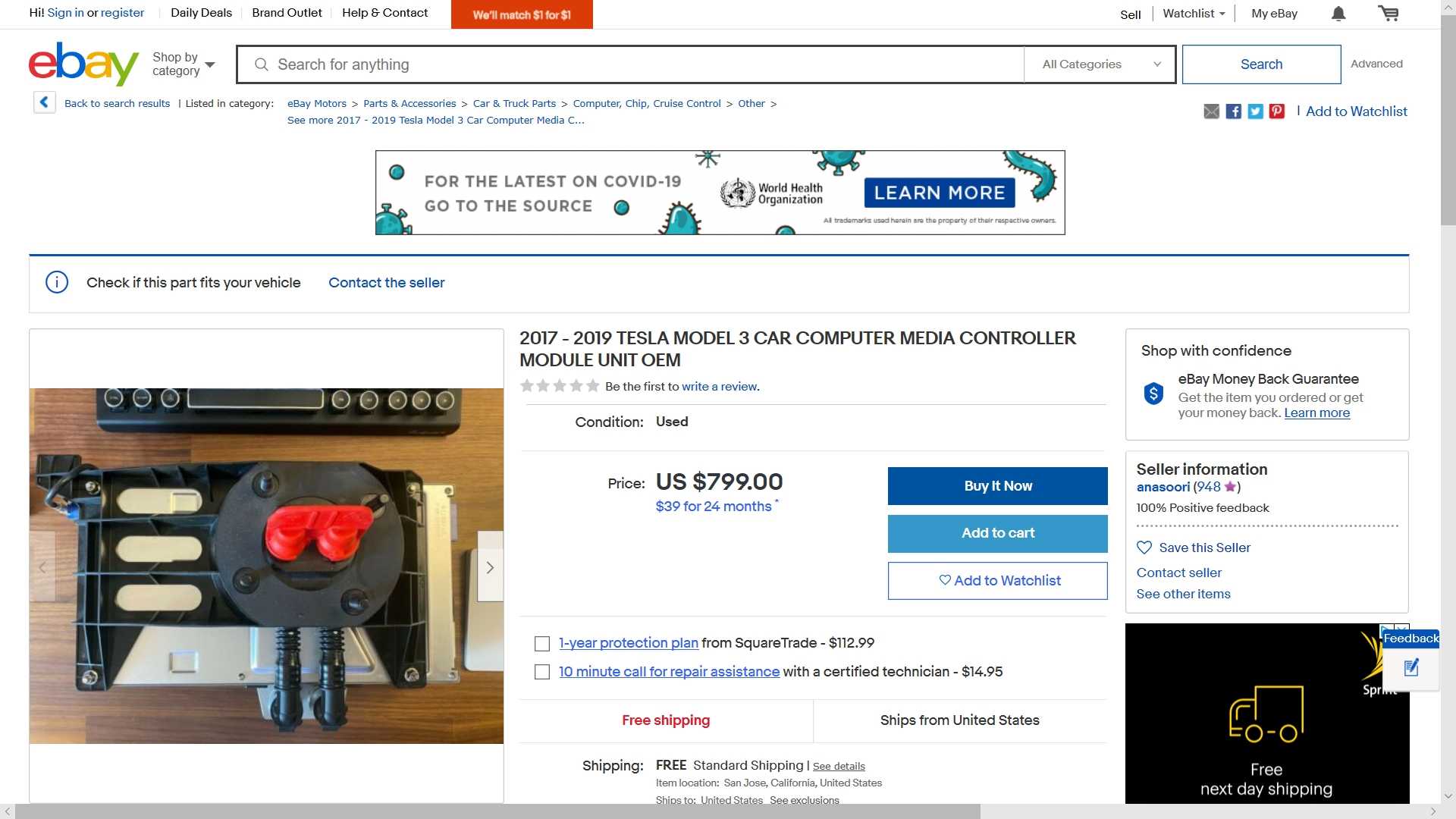
Green allegedly obtained four Tesla MCUs (media control units) from eBay and found that the previous owners personal data was still present and freely accessible.
Ordinarily, a car’s infotainment system would store things like phone numbers, addresses, and audio media. But because this is a Tesla, it has Netflix and Spotify. Some of the systems were also found to store Netflix session cookies, which can then be used to gain access to the owner’s account.
The car was also found to store Gmail cookies and all previously-used WiFi passwords. Spotify passwords are also stored in plain text, according to Green.
In particular if you log into spotify – the password is stored in plain text. gmail and netflix are stored as a cookie but still give a potential attacker access.
The of course all recent calendar events and your phone book and calls history too.— green (@greentheonly) May 3, 2020
Green told InsideEVs that each of the modules he bought had the “owner’s home and work location, all saved WiFi passwords, calendar entries… call lists and address books from paired phones, Netflix and other stored session cookies.”
Tesla began offering the retrofit service in March this year. The company offers the service to let owners of older models upgrade their hardware to gain access to new Tesla features that require more processing power.
Only Tesla is able to perform these retrofits, and because most owners want their personal data transferred to the new unit — so they don’t have to set everything up again — they hand over their vehicles without wiping their data.
The issue is that the owner doesn’t ever see their original MCU again.
Green got in touch with Tesla over a week before making their findings public. As of yesterday, the EV company still hadn’t contacted customers that could be affected by this whole oversight.
Tesla service centers are supposed to destroy the hardware after its removed the vehicle. Indeed, one of the devices Green obtained had been crushed, but even so, this isn’t enough to wipe data from the device.
In many cases, the devices aren’t damaged as units that are still functioning fetch more on the second-hand market.
It’s been more than a week, and Tesla is yet to clarify its process for handing used hardware with InsideEVs.
What’s more concerning is that it’s not entirely clear how the hardware is making it onto the second-hand market. It seems Tesla service centers are under instruction to destroy the hardware and throw it out (hopefully to be recycled). But evidently, that’s not happening.
It should be noted that this kind of phenomenon is not necessarily unique to Tesla.
Last month, British consumer advice magazine Which? found that Ford and Volkswagen’s infotainment systems can compromise user data in a similar fashion.
If you’re selling your car, be sure to wipe your data yourself. Cars store so much data these days you should think of it like selling a laptop.
If you’re having your Tesla MCU replaced, do everything you can to make sure Tesla is wiping the unit before disposing of it. If you had it replaced recently, it makes sense to change potentially compromised passwords, now.
Corona coverage
Read our daily coverage on how the tech industry is responding to the coronavirus and subscribe to our weekly newsletter Coronavirus in Context.
For tips and tricks on working remotely, check out our Growth Quarters articles here or follow us on Twitter.
